Friday, May 28, 2010
Sinatra Step 8
What is MongoHQ?
MongoDB is a scalable, high-perfomance, open source, document-oriented database written using C++. It actually creates a bridge between traditional RDBMS and data storage key.
How does MongoDB relates to MongoHQ?
MongoHQ provides a hosting platform for MongoDB and also uses MongoDB as the back-end tool for its applications. MongoHQ is the hosted database solution for easily uploading your application and running with MongoDB.
References
MongoDB (2010). The best features of document databases key – Value stores, andRDBMSes. Retrieved from www.Mongodb.org
B) What is Mongo Mapper?
“MongoMapper is ruby wrapper library which aims to make using MongoDB in easy and user friendly way.” Github(2010)
As we know MongoDB stores data, MongoMapper consists two key concepts to makes process simple. The two concepts are Document and EmbeddedDocument.
References
Github (2010). MongoMapper. Retrieved from http://wiki.github.com/jnunemaker/mongomapper/
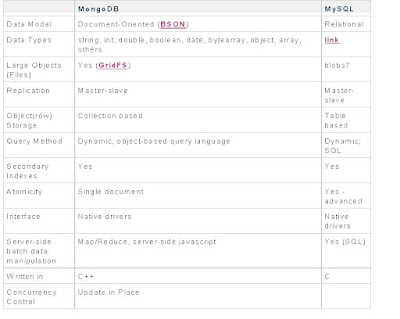
C) What is the relation between MongoDB and Mysql?
According to mongodb.org (2010) there are few similarities between MongoDB and Mysql. The below table explain them all.
References
mongoDB (2010). MongoDB, CouchDB, MySQL Compare Grid . Retrieved from http://www.mongodb.org/display/DOCS/MongoDB,+CouchDB,+MySQL+Compare+Grid
MongoDB is a scalable, high-perfomance, open source, document-oriented database written using C++. It actually creates a bridge between traditional RDBMS and data storage key.
How does MongoDB relates to MongoHQ?
MongoHQ provides a hosting platform for MongoDB and also uses MongoDB as the back-end tool for its applications. MongoHQ is the hosted database solution for easily uploading your application and running with MongoDB.
References
MongoDB (2010). The best features of document databases key – Value stores, andRDBMSes. Retrieved from www.Mongodb.org
B) What is Mongo Mapper?
“MongoMapper is ruby wrapper library which aims to make using MongoDB in easy and user friendly way.” Github(2010)
As we know MongoDB stores data, MongoMapper consists two key concepts to makes process simple. The two concepts are Document and EmbeddedDocument.
References
Github (2010). MongoMapper. Retrieved from http://wiki.github.com/jnunemaker/mongomapper/
C) What is the relation between MongoDB and Mysql?
According to mongodb.org (2010) there are few similarities between MongoDB and Mysql. The below table explain them all.
References
mongoDB (2010). MongoDB, CouchDB, MySQL Compare Grid . Retrieved from http://www.mongodb.org/display/DOCS/MongoDB,+CouchDB,+MySQL+Compare+Grid
Elevator Speech 2
Besides I put at Elevator Pitch 1, I found a very good discussion on “business-know-how” of how to write a good elevator pitch. It is called “The Art of the Elevator Pitch” at http://www.businessknowhow.com/money/elevator.htm
It puts down six questions a good elevator pitch must ask:
1. What is your product or service?
2. Who is your market?
3. What is your revenue model?
4. Who is behind the company?
5. Who is your competition?
6. What is your competitive advantage?
Exercise 10 : Concurrency and Threading demonstration in Phyton
1. Find definitions for eight terms and concepts used in threaded programming:
1. Thread Synchronisation
Synchronization enables you to control program flow and access to shared data for concurrently executing threads.The four synchronization models are mutex locks, read/write locks, condition variables, and semaphores.
· Mutex locks allow only one thread at a time to execute a specific section of code, or to access specific data.
· Read/write locks permit concurrent reads and exclusive writes to a protected shared resource. To modify a resource, a thread must first acquire the exclusive write lock. An exclusive write lock is not permitted until all read locks have been released.
· Counting semaphores typically coordinate access to resources. The count is the limit on how many threads can have concurrent access to the data protected by the semaphore. When the count is reached, the semaphore causes the calling thread to block until the count changes. A binary semaphore (with a count of one) is similar in operation to a mutex lock.
2. Locks
Most applications require threads to communicate and synchronize their behavior to one another. The simplest way to accomplish this task in a program is with locks. To prevent multiple accesses, threads can acquire and release a lock before using resources. Imagine a lock on the copy machine for which only one worker can possess a key at a time. Without the key, use of the machine is impossible. Locks around shared variables allow threads to quickly and easily communicate and synchronize. A thread that holds a lock on an object knows that no other thread will access that object. Even if the thread with the lock is preempted, another thread cannot acquire the lock until the original thread wakes up, finishes its work, and releases the lock. Threads that attempt to acquire a lock in use go to sleep until the thread holding the lock releases it. After the lock is freed, the sleeping thread moves to the ready-to-run queue.
For example, In Java programming, each object has a lock; a thread can acquire the lock for an object by using the
synchronized keyword. Methods, or synchronized blocks of code, can only be executed by one thread at a time for a given instantiation of a class, because that code requires obtaining the object's lock before execution. Continuing with our copier analogy, to avoid clashing copiers, we can simply synchronize access to the copier resource, allowing only one worker access at a time, as shown in the following code sample. We achieve this by having methods (in the Copier object) that modify the copier state be declared as synchronized methods. Workers that need to use a Copier object have to wait in line because only one thread per Copier object can be executing synchronized code.3. Deadlock
Deadlocking is a classic multithreading problem in which all work is incomplete because different threads are waiting for locks that will never be released. Imagine two threads, which represent two hungry people who must share one fork and knife and take turns eating. They each need to acquire two locks: one for the shared fork resource and one for the shared knife resource. Imagine if thread "A" acquires the knife and thread "B" acquires the fork. Thread A will now block waiting for the fork, while thread B blocks waiting for the knife, which thread A has. Though a contrived example, this sort of situation occurs often, albeit in scenarios much harder to detect. Although difficult to detect and hash out in every case, by following these few rules, a system's design can be free of deadlocking scenarios:
- Have multiple threads acquire a group of locks in the same order. This approach eliminates problems.
- Group multiple locks together under one lock. In our case.
- Label resources with variables that are readable without blocking.
- Most importantly, design the entire system thoroughly before writing code. Multithreading is difficult, and a thorough design before you start to code will help avoid difficult-to-detect locking problems.
4. Semaphores
Frequently, several threads will need to access a smaller number of resources. For example, imagine a number of threads running in a Web server answering client requests. These threads need to connect to a database, but only a fixed number of available database connections are available. How can you assign a number of database connections to a larger number of threads efficiently? One way to control access to a pool of resources (rather than just with a simple one-thread lock) is to use what is known as a counting semaphore. A counting semaphore encapsulates managing the pool of available resources. Implemented on top of simple locks, a semaphore is a thread-safe counter initialized to the number of resources available for use. For example, we would initialize a semaphore to the number of database connections available. As each thread acquires the semaphore, the number of available connections is decremented by one. Upon consumption of the resource, the semaphore is released, incrementing the counter. Threads that attempt to acquire a semaphore when all the resources managed by the semaphore are in use simply block until a resource is free.
5. Mutex (mutual exclusion)
Use mutual exclusion locks (mutexes) to serialize thread execution. Mutual exclusion locks synchronize threads, usually by ensuring that only one thread at a time executes a critical section of code. Mutex locks can also preserve single-threaded code.
To change the default mutex attributes, you can declare and initialize an attribute object. Often, the mutex attributes are set in one place at the beginning of the application so the attributes can be located quickly and modified easily.
6. Thread
A program or process can contain multiple threads that execute instructions according to program code. Like multiple processes that can run on one computer, multiple threads appear to be doing their work in parallel. Implemented on a multi-processor machine, they actually can work in parallel. Unlike processes, threads share the same address space; that is, they can read and write the same variables and data structures.
7. Event
Events are the actual part or state of the programme. The programme is made up with the series of the events. In the event driven programme the flow of programming resolve by events. In the programme, start from the main event and dispatch or compile the all written events and quiet with the end event.
8. Waitable timer.
This Wait-Event represents the amount of time a user or application has “slept” through the different procedures in many languages. Normally, the waitable timer procedures have keywords like wait, sleep, idle, timer.sleep, LOCK.sleep etc.
References:
Ales Roetter. (2001, February 01). Concurrent programming : Writting multithreaded java application. Retrieved May 27, 2010, from IBM developerWorks: http://www.ibm.com/developerworks/library/j-thread.html#h2
Blaise Barney. (2010, January 14). POSIX Threads Programming. Retrieved May 28, 2010, from Lawrence Livermore National Laboratory : Computing: https://computing.llnl.gov/tutorials/pthreads/#Designing
2. A simple demonstration of the threading module in Python (threaddemo.py) that uses both a lock and semaphore to control concurrency is by Ted Herman at the University of Iowa. The code and sample output below are worth a look. Report your findings.
threaddemo.py
Here, we have total 9 threads which are running simultaneously with the proper use of multitasking. Program includes the use of many concepts such as random numbers, time operations, waitable timers etc. In this programme maximum number of tasks run at the same time is 3. But which task finish first is depends on the priority set randomly in the program. Programmer had done well after printing all the function such as showing how many tasks are running, which task will run for how much time, which thread is finish and which task is now started etc. In the beginning the first three tasks will run with same priority while other tasks are in waiting list. As soon as any task will finish the message will display with current progress and one task will be start and will show in current process. The new task will be start until all remaining tasks started running. After end of each thread, a new thread will be added. Program will run till the end of all threads.
Exercise 11: TP monitors and transaction protocols
For example, enrolling a patient in a health care plan may involve first acquiring release forms from the patient, verifying the patient's employment, checking her health and insurance history against remote data sources, and so on. All of the activities described can be subtasks of a single transaction, because failure of any one of these subtasks should cause the entire transaction to fail.
Enterprise transactions share the properties of atomicity, consistency, isolation, and durability, denoted by the acronym ACID. These properties are necessary to ensure safe data sharing.
Atomicity
The rule of atomicity is the transaction must follow all the conditions made by the designer of the database. If not then database remain unchanged. For example some field must not be empty etc. The transaction cannot be divided in parts and must be perform in the conditions of all or nothing. It reduce the some pressure of the database administrator after making sure that no incomplete or wrong transaction allowed by the end-user.
Atomicity means that a transaction is considered complete if and only if all of its operations were performed successfully. If any operation in a transaction fails, the transaction fails. In the health care example, a patient can be enrolled only if all required procedures complete successfully, so enrollment is atomic.
Consistency
Consistency means that a transaction must transition data from one consistent state to another, preserving the data's semantic and referential integrity. For example, if every health care policy in a database requires both a patient covered by the policy and a plan describing the coverage, every transaction in the health insurance application must enforce this consistency rule. While applications should always preserve data consistency, many databases provide ways to specify integrity and value constraints so that transactions that attempt to violate consistency will automatically fail
Isolation
Isolation means that any changes made to data by a transaction are invisible to other concurrent transactions until the transaction commits. Isolation requires that several concurrent transactions must produce the same results in the data as those same transactions executed serially, in some (unspecified) order. In the health plan enrollment example, isolation ensures that updates made to a patient record will not be globally visible until those updates are committed
Durability
Durability means that committed updates are permanent. Failures that occur after a commit cause no loss of data. Durability also implies that data for all committed transactions can be recovered after a system or media failure.
An ACID transaction ensures that persistent data always conform to their schema, that a series of operations can assume a stable set of inputs and working data, and that persistent data changes are recoverable after system failure.
References
SUN Microsystems. (2002). Transactional Concepts . Retrieved May 27, 2010, from Designing Enterprise Applications with the J2EETM Platform, Second Edition: http://java.sun.com/blueprints/guidelines/designing_enterprise_applications_2e/transactions/transactions2.html
2. Describe a TP monitor environment. How can a TP monitor stop an operating system being overwhelmed?
TP Monitor or Transaction Processing monitor, which is a control program who manages the transfer of data between multiple local and remote terminals and the application programs that serve them. It may include programs that format the terminal screens and validate the data entered.
TP monitor assists to allocate the processes across the application and database server and stop an overwhelmed of the operating system. TP monitor operates as a load balancer which stabilities the load of a system after balancing the load of assigned processes to another machine in a distributed client/server environment. A TP monitor also augments the statement that all databases are updated from a single transaction.
TP monitor assists to allocate the processes across the application and database server and stop an overwhelmed of the operating system. TP monitor operates as a load balancer which stabilities the load of a system after balancing the load of assigned processes to another machine in a distributed client/server environment. A TP monitor also augments the statement that all databases are updated from a single transaction.
Reference:
Free Online Encyclopedia 2010, TP monitor definition of TP monitor in the Free Online Encyclopedia, viewed 28 April 2010, http://encyclopedia2.thefreedictionary.com/TP+monitor
Free Online Encyclopedia 2010, TP monitor definition of TP monitor in the Free Online Encyclopedia, viewed 28 April 2010, http://encyclopedia2.thefreedictionary.com/TP+monitor
Puntti, Tanya. (2007). “Database Application Development”. TP Monitors in large database systems. Retrieved 26th May 2010 from: http://www.hypergurl.com/blog/databases/architecture-tp-monitor.html
Wikipedia 2010, Transaction processing system, last modified 21 April 2010, viewed 28 April 2010,
http://en.wikipedia.org/wiki/Transaction_processing_system
http://en.wikipedia.org/wiki/Transaction_processing_system
Exercise 14: Searching mechanisms, virtual worlds and cyberagents
1. What is a spider? What does it do?
Spider is a program that visits Web sites and reads their pages and other information in order to create entries for a search engine index. The Spiders are typically programmed to visit sites that have been submitted by their owners as new or updated. Entire sites or specific pages can be selectively visited and indexed. Spiders are called spiders because they usually visit many sites in parallel at the same time, their “legs” spanning a large area of the “web.” Spiders can crawl through a site’s pages in several ways.
References
Tech Target. (n.d.). Cloud/Internet Technology. Retrieved May 25, 2010, from Whatis.com techtarget Search: http://whatis.techtarget.com/definition/0,,sid9_gci213035,00.html
2. Differentiate the various types of software agents.
Ø Collaborative Agents
Ø Interface Agents
Ø Mobile Agents
Ø Information Agents
Ø Reactive Agents
Ø Reactive Agents
Ø Hybrid Agents
Ø Heterogeneous Agent Systems
Ø Smart Agents
3. Identify various activities in e-commerce where software agents are currently in use.
If you notice entries like Teleprot Pro and WebStripper in your traffic reports, someone’s been busy attempting to download your web site. You don’t have to just sit back and let this happen. If you are commercially hosted, you’ll have to just sit back and let this happen. If you are commercially hosted, you’ll be able to add a couple of lines to your robots.txt file to prevent repeat offenders from stripping your site.
The robots.txt file gives search engine spiders and agents direction by informing them what directories and files they are allowed to examine and retrieve. These rules are called The Robots Exclusion Standard.
References:
Bloch, M. (n.d.). Robots, Agents and Spiders - Identifying Search Engine Crawlers. Retrieved may 22, 2010, from Taming the Beast: http://www.tamingthebeast.net/articles2/search-engine-spiders.htm
4. Computing ethics and bot programming case study: rocky
Rocky is an ELIZA-like bot.
This was the most funny part of assignments and found is like i am not doing my study, i had check the question twice to making myself sure that yes i understand the question right below are my findings.
train1 activates Rocky.
Rocky says, "Gee thanks for waking me up! I must have dozed off.."
You say, "Hello"
Rocky says, "Do you have any hobbies?"
You say, "Watching football mate"
Rocky says, "What exactly are we talking about?"
You say, "i think you don’t know who is maradona, Do you?"
Rocky says, "You think you don’t know who is maradona Do me? Why?"
You say, "oh my mistake"
Rocky says, "Is your mistake important to you?"
You say, "you are like a baby"
You say, "i love baby"
Rocky [to train1]: Why do you think I am like baby?
Rocky says, "Why do you say you love me?"
I don't understand that.
You say, "because you just react like a baby"
Rocky says, "What are you like at programming in Python?"
You say, "i would rather working in JAVA than working in Python"
Rocky says, "Um, i get the feeling this conversation is not going anywhere.."
I don't understand that.
You say, "me too"
Rocky says, "Where'd you think up a name like 'train1' anyway?"
You say, "so why dont we stop what you think?"
Rocky says, "I like the way you bring up such great topics to discuss.."
You say, "okk than good bye"
Rocky [to train1]: Goodbye, catch ya later
You say, "have a nice day"
Exercise 15: M-commerce: Innovation and mobile devices
1. What is meant by a location based service? Explain using the Web applications found on a late model mobile device?
Alliance
4. Visit an Airline Web site and search information on WAP or SMS or 3G mobile application access to booking airline services. The same services exist in banking. How do both industries compare?
As Wikipedia (2010) says, LBS (Local Based Service) is an information and entertainment service, accessible with mobile devices through the mobile network and utilizing the ability via mobile devices through mobile network and utilizing the ability to make use of the geographical position of the mobile device.
There are many areas where LBS can be useful. Nowadays we can see LBS in many web applications like navigation services (like GPS), traffic alerts, hospital alerts, local businesses alert, location based mobile advertising etc.
References
2. Describe the purpose of the Open Mobile Alliance
Wikipedia (2010). Open Mobile Alliance
3. What are the main components of a mobile Web services framework?
Mobile Server
The Mobile Server is a mobile remote computer; linked to the Internet via an Inmarsat Regional Broadband Global Area Network (RBGAN) User Terminal (UT) The mobile web services are active on this server. The mobile Server could be used as a server or as a client PC and it just accept requests from the Gatekeeper
The Gatekeeper is placed on the terrestrial Internet, and acts as the sole gateway to the Mobile Server. It is used to perform authentication and authorization of requests before sending them to the Mobile Server. Moreover, the Gatekeeper store buffered data, so it will enable more economic usage of the satellite link.
The physical connection between the remote web server and the Gatekeeper is established using a Satellite Access Station, a Telecommunications Satellite and a satellite modem.
The mobile Server is connected to a set of peripherals, such as a GPS device, a web cam or a Data Acquisition system. From these devices, data is collected by the web service.
The Gatekeeper handles requests from clients over the Internet. A client can be a PC with a web browser, or another application using a http Simple Object Application Protocol – SOAP request.
What is WAP?
WAP (Wireless Application Protocol) is a leading global open standard for wireless services over phone networks. It allows you to access Internet content via wireless devices such as your mobile phone or PDA. You can then access information even while on the go.
What are GPRS and 3G?
General Packet Radio Service (GPRS) is a packet-data technology that allows mobile users to connect to the Internet at up to 115kbps. GPRS is a vital step in the evolution to third-generation (3G) mobile services. With 3G mobile networks, broadband multimedia communication will soon be realised.
In Singapore airlines you can access the following mobile services:
- Real-time flight information
- Our worldwide office addresses, telephone/fax numbers and email addresses
- Flight alerts to be sent to your mobile/pager/email address
- KrisFlyer Redemption and Accrual Calculators
- Exclusive KrisFlyer Promotions & Events Listings
In Commonwealth Bank you can register your mobile number in the section of net bank security code send to you by commbank server to your mobile phone device as a SMS. Commonwealth bank Australia is using WAP technology to send information about stock prices once or twice a day to registered customers with the help of Optus and Telstra.
References
Singapore Airlines. (n.d.). Mobile Services: before you fly FAQ - Mobile Services. Retrieved may 25, 2010, from Singapore AIR: http://www.singaporeair.com/saa/en_UK/content/before/travelfaq/mobileservices.jsp
Subscribe to:
Comments (Atom)